Table of contents
Update: Saturday 10th February 2024.
Update: Wednesday 28th February 2024.
TL;DR.
LXD (LinuXDaemon) is a container manager for creating and managing containers. LXCs (LinuXContainers) are isolated system instances where anything within the container can NOT affect other containers or the base distro/OS. Also, multiple container instances can run concurrently on a single host.
Attributions:

An Introduction.
This is a concise (read: less rambling) version of a post from 2023. This time around, I will be more specific about my intentions for this adapted chronicle.
The purpose of this post is to present the installation, and likely uses, of LXD/LXC.

The Big Picture.
Containers are considered the Second Wave of System Isolation Technologies. The First Wave were virtual machines and the Third Wave are WASM/WASI binaries. Each Wave brought their own strengths and weaknesses.
| Name | Advantage | Disadvantage |
| Wave 1: Virtual Machines | Isolation, less hardware, systems isolation, security, multiple OSs, ISA. | Resource heavy, expensive, complex. |
| Wave 2: Containers | Isolation, reduced complexity, security, distributed computing, consistency, orchestration, portability, efficiency, scalability, automation, shared kernel. | Stateless, may be hard to network, compatibility with other container technologies, |
| Wave 3: WASM | Portable, assemblies not needed after compilation, can run outside the browser with WASI. | Download size on Edge/2G and GSM/3G, not aware of the DOM - yet, lacks standard security defences. |

Prerequisites.
- A Linux-based distro (I use Ubuntu).

Updating the System.
- I update my system:
sudo apt clean && \
sudo apt update && \
sudo apt dist-upgrade -y && \
sudo apt --fix-broken install && \
sudo apt autoclean && \
sudo apt autoremove -y
What is LXD and LXC?
The LXD (LinuX Daemon) is the container manager that is used to create, and manage, LXCs (LinuX Containers). It is a background service that can automatically start LXCs when the host system boots, or stop any container from starting at all.
An LXC (LinuX Container) is an isolated, OS-level virtualization which, for efficiency, uses the Linux kernel of the host system. An LXC is a virtual environment where system processes within the LXC container can not affect other containers, or the host system, without specifically running certain commands.
https://ubuntu.com/server/docs/containers-lxd↗,
https://ubuntu.com/server/docs/containers-lxc↗, and
https://solodev.app/installing-lxd-and-using-lxcs.
Installing the LXD.
- I install the snap package manager, if required:
sudo apt install -y snapd
- I install the LXD manager:
sudo snap install lxd
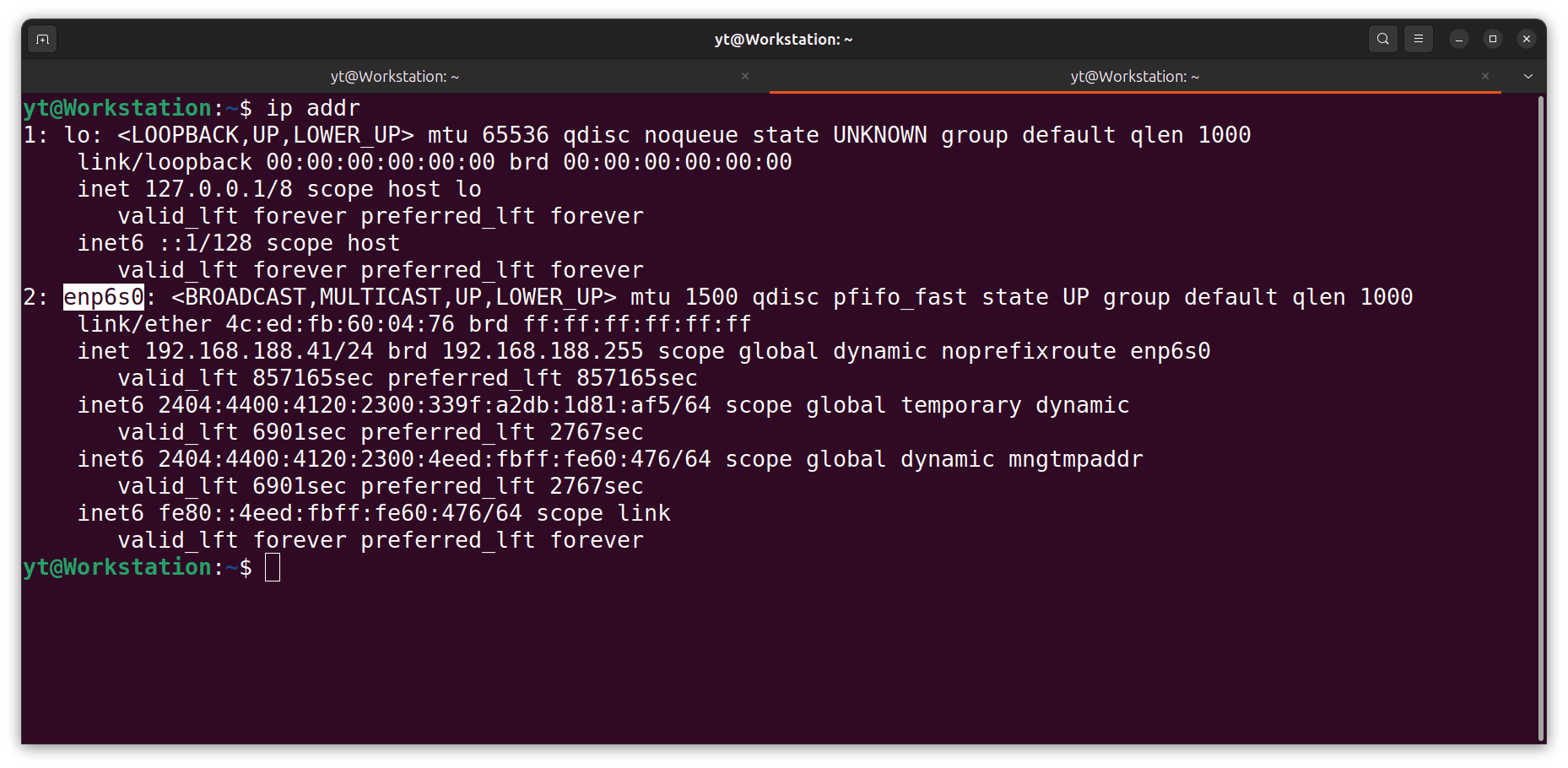
- I find the name of my host interface:
ip addr
NOTE: My host interface name for the NIC (network interface card) is enp6s0.
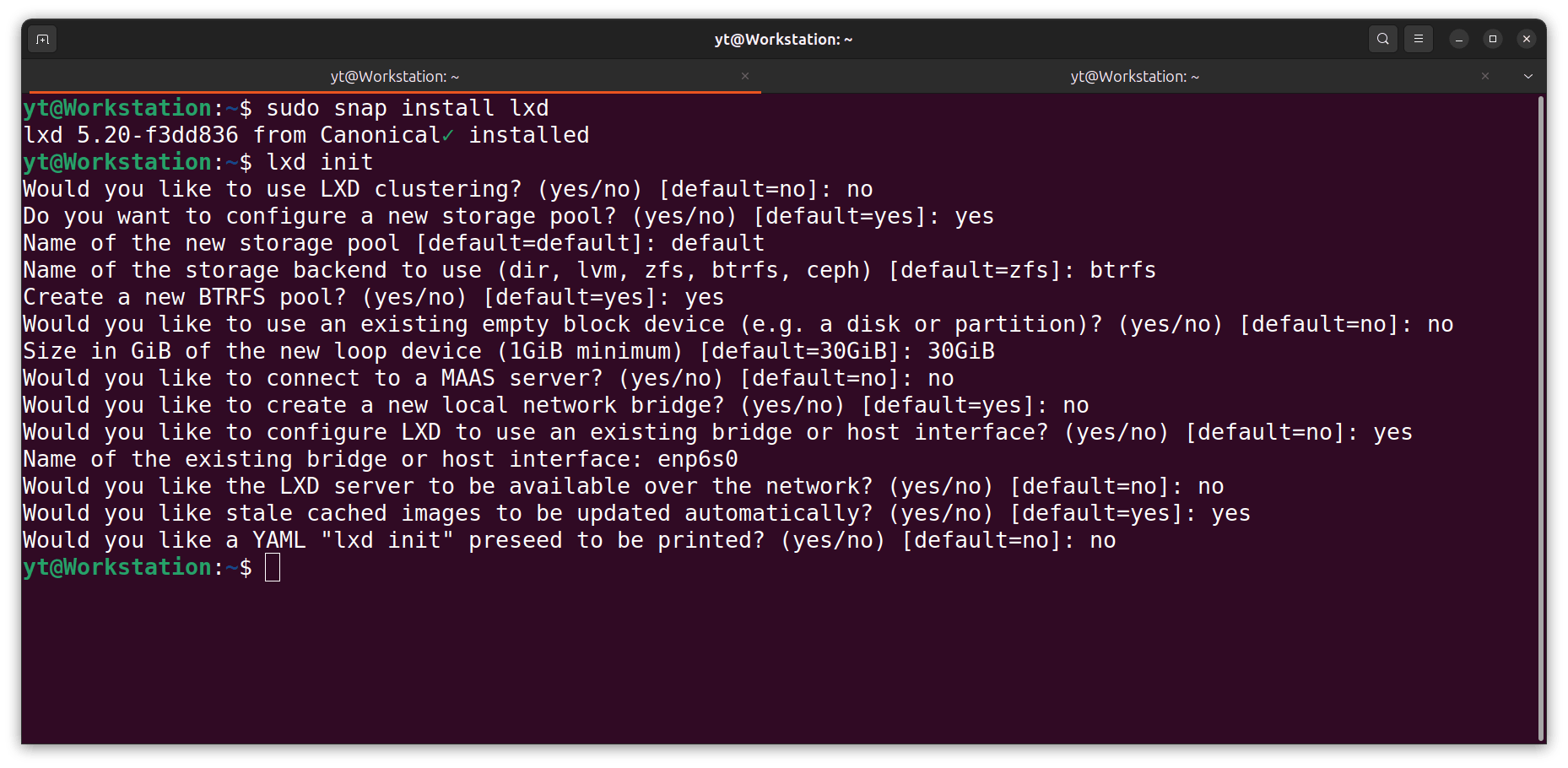
- I initialise the LXD:
lxd init
NOTE: When initialised, the host interface (enp6s0) will become available to the LXD manager. Now the LXD manager can connect to the router and ask for IP addresses for any running containers.
Troubleshooting.
- I run a simple
LXCcommand:
lxc ls
- Running the
LXCcommand may result in one of these errors:
Error: Failed to connect to local LXD: Get "http://unix.socket/1.0": dial unix /var/snap/lxd/common/lxd/unix.socket: connect: permission denied
bash: /usr/sbin/lxc: No such file or directory
- To fix this issue, I provide access to the LXD group for my current account:
sudo usermod -aG lxd $(whoami)
- I change the GID (group ID) for the
LXDmanager:
newgrp lxd
- I test these changes by running the
LXCcommand again:
lxc ls
Deleting the LXD.
- I can delete the LXD, if required:
sudo snap remove --purge lxd
NOTE: The
--purgeflag removes everything, including configuration files, etc.
Setting Up an LXC.
- I list the existing containers:
lxc ls
- I launch a new container called Default:
lxc launch ubuntu:22.04 Default
- I bash into the container:
lxc exec Default -- bash
- I update and upgrade the container:
sudo apt clean && \
sudo apt update && \
sudo apt dist-upgrade -y && \
sudo apt --fix-broken install && \
sudo apt autoclean && \
sudo apt autoremove -y
Adding a User Account to the LXC.
- From within the container, I add a new user:
adduser yt
- I add the new user to the
sudogroup:
usermod -aG sudo yt
NOTE: usermod let's me (-a)ppend the sudo (-G)roup to the yt account.
- I exit the container:
exit
NOTE: I exit the
rootaccount to use theytaccount.
Setting the LXC Home Directory.
- From the terminal, I log in to the container with the
ytaccount:
lxc exec Default -- su yt
NOTE: At the moment, the home directory is
/root. This section will address the issue by changing the home directory to~.
- I use the Nano text editor to open the
.bashrcfile:
sudo nano ~/.bashrc
- I copy the following, add it (CTRL + SHIFT + V) to the bottom of the
.bashrcfile, save (CTRL +S) the changes, and exit (CTRL + X) Nano:
cd ~
Hardening the Container.
- From within the container, I use the
Nanotext editor to open thesshd_configfile:
sudo nano /etc/ssh/sshd_config
- I copy the following, add it (CTRL + SHIFT + V) to the bottom (CTRL + END) of the
sshd_configfile, save (CTRL +S) the changes, and exit (CTRL + X) Nano:
PasswordAuthentication no
PermitRootLogin no
Protocol 2
Port 22
NOTE: Port 22 is the default, so I'll choose my own, random, available port number.
- I restart the "ssh" service:
sudo systemctl restart ssh.service
- I reboot the container:
sudo reboot
NOTE: Within the container, I can also install (or enable) UFW, Fail2Ban, and CrowdSec.
23 Common Commands.
Here is a list of 23 commands that maybe somewhat useful. Although I commonly use only a handful of commands from this list, it's nice to have a reference on file:
lxc --versionto check the version (and if the command doesn't work, then I'd know an installation problem occurred),lxc network listto list all the network adapters,lxc init ubuntu:22.04 test-container3to download an Ubuntu container,lxc launch ubuntu:22.04 test-container3to launch an Ubuntu container,lxc storage lsto list storage pool,lxc listorlxc lsto list all the images and containers,lxc stop test-container3to stop a container,lxc start test-container3to start a container,lxc restart test-container3to restart a container,lxc stop test-container3followed bylxc delete test-container3, orlxc stop test-container3 -fto delete a container,lxc exec test-container3 cat /etc/os-releaseto execute a command on the container,lxc info test-container3to check a container's Information,lxc exec test-container3 -- bashto get root access to a container,lxc exec test-container3 -- su myloginto get account access to a container,lxc copy test-container3 test-container3-cloneto copy a container,lxc image list images: | grep -i centosto list prebuilt images,lxc network show lxdbr0to display information about network interface(s),lxc profile show defaultto check the default profile using lxc command,lxc snapshot test-container3 test-container3_snapfollowed bylxc info test-container3to take snapshot of an instance,lxc restore test-container3 test-container3_snapto restore an instance from a snapshot,lxc export test-container3 /root/backup/lxd/test-container3_bkp--$(date +'%m-%d-%Y').tar.xz --optimized-storageto take backup of an instance,lxc import /root/backup/lxd/test-container3_bkp--05-07-2022.tar.xzfollowed bylxc listto restore instance from a backup, andlxc --helpto check all the options that are available to an LXC command.
Attribution:
https://www.cyberithub.com/20-best-lxc-command-examples-to-manage-linux-containers/

The Results.
LXD and LXC provide a powerful, flexible, and resource-efficient way to run isolated system instances on a single host. This technology represents the second wave of system isolation technologies, offering certain advantages over traditional virtual machines. The process of installing LXD and using LXC may seem complex at first, but once I understood the basics and familiarized myself with common commands, I could create, manage, and delete containers with ease. Whether I'm setting up a homelab or deploying applications in a production environment, mastering LXD/LXC is a valuable skill.
In Conclusion.
LXD and LXC was a revolutionary system isolation technology. LXD (Linux Daemon) is a container manager that allows me to create and manage containers. LXCs (Linux Containers), on the other hand, are isolated system instances. They ensure that anything within the container doesn't affect other containers or the base operating system. This means multiple container instances can run concurrently on a single host.
Containers are considered the Second Wave of System Isolation Technologies. The First Wave were virtual machines and the Third Wave are WASM/WASI binaries. Each Wave brought their own strengths and weaknesses.
LXD and LXC provide a powerful, flexible, and resource-efficient way to run isolated system instances on a single host. This technology offers certain advantages over traditional virtual machines, making it a valuable skill to master.
Once I understood the basics, I could create, manage, and delete containers with ease. Whether setting up a homelab or deploying applications in a production environment, adopting LXD/LXC was a game-changer.
So, have you used LXD and LXC in your projects? What's your experience been like? Share your thoughts in the comments below!
Until next time: Be safe, be kind, be awesome.
NOTE: All images generated by ComfyUI using the dreamshaper_8 checkpoint.